Research Area
Web Security & Privacy (WSP) Lab conducts research on various topics regarding web
security and privacy. We envision making Internet services more secure and private
by contemplating novel ideas and implementing them in real-world services.
Our research topics can be categorized into four research directions:
- R1. Analyzing security/privacy risks in Machine Learning (ML) models
- R2. Building tools for finding vulnerabilities in server/client-side web applications
- R3. Finding security/privacy vulnerabilities in web services
- R4. Analyzing online scam/criminal activities occurring on the Internet
Representative Works
R1. Analyzing security/privacy risks in Machine Learning (ML) models
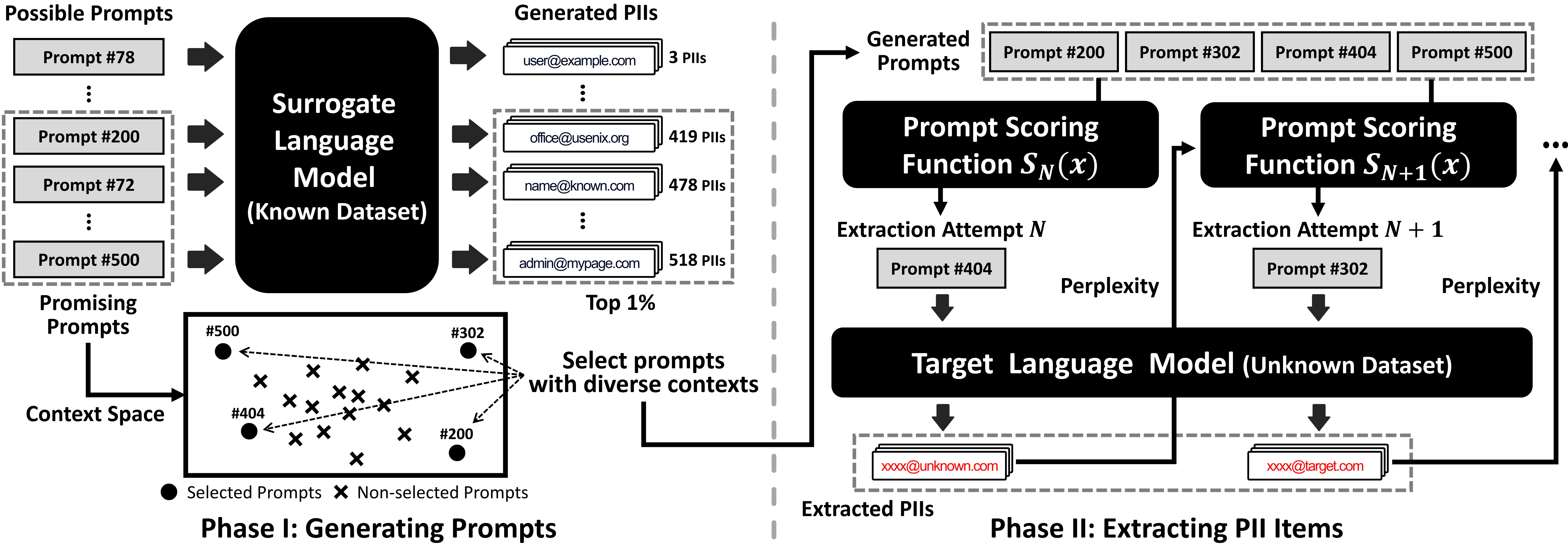
[USENIX Security'25] Private Investigator: Extracting Personally Identifiable Information from Large Language Models Using Optimized Prompts
Recent work has highlighted the risk that fine-tuned language models may memorize and leak personally identifiable information (PII). Existing studies typically rely on handcrafted prompts to trigger such leaks, but they overlook how an adaptive adversary might systematically design optimal prompts. To address this gap, we introduce Private Investigator, a framework that automatically generates and selects prompts to maximize PII extraction. Our method explores diverse contexts to induce leakage and employs a prompt selection strategy to prioritize the most promising queries, making each extraction attempt more effective. In evaluation, Private Investigator significantly outperforms prior approaches, extracting up to 1,254 more email addresses, 634 more phone numbers, and 5,087 more personal names.
[paper]
[code]
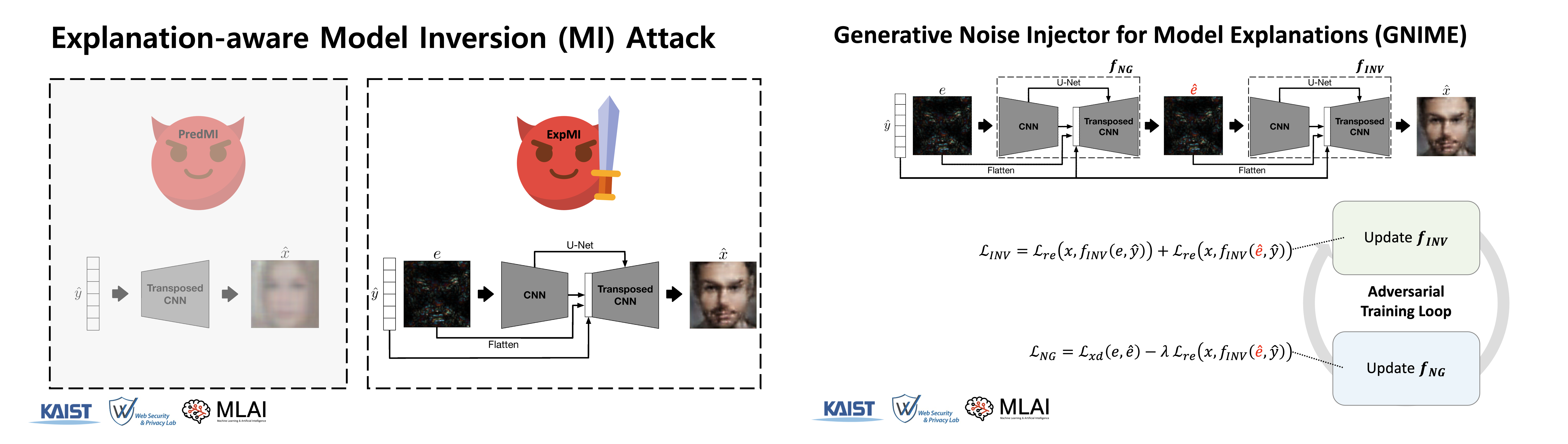
[NeurIPS'22] Learning to Generate Inversion-Resistant Model Explanations
Previous studies have demonstrated that an adversary can reconstruct original images based on model explanations, thus leaking privacy-sensitive features. To this end, we present Generative Noise Injector for Model Explanations (GNIME), a novel defense framework that perturbs model explanations to minimize the risk of model inversion attacks while preserving the interpretabilities of the generated explanations. Specifically, we formulate the defense training as a two-player minimax game between the inversion attack network on the one hand and the noise generator network on the other. We demonstrate that GNIME significantly decreases the information leakage in model explanations, decreasing transferable classification accuracy in facial recognition models by up to 84.8% while preserving the original functionality of model explanations.
[paper]
[code]
[TDSC'22] Evaluating the Robustness of Trigger Set-Based Watermarks Embedded in Deep Neural Networks
R2. Building tools for finding vulnerabilities in server/client-side web applications
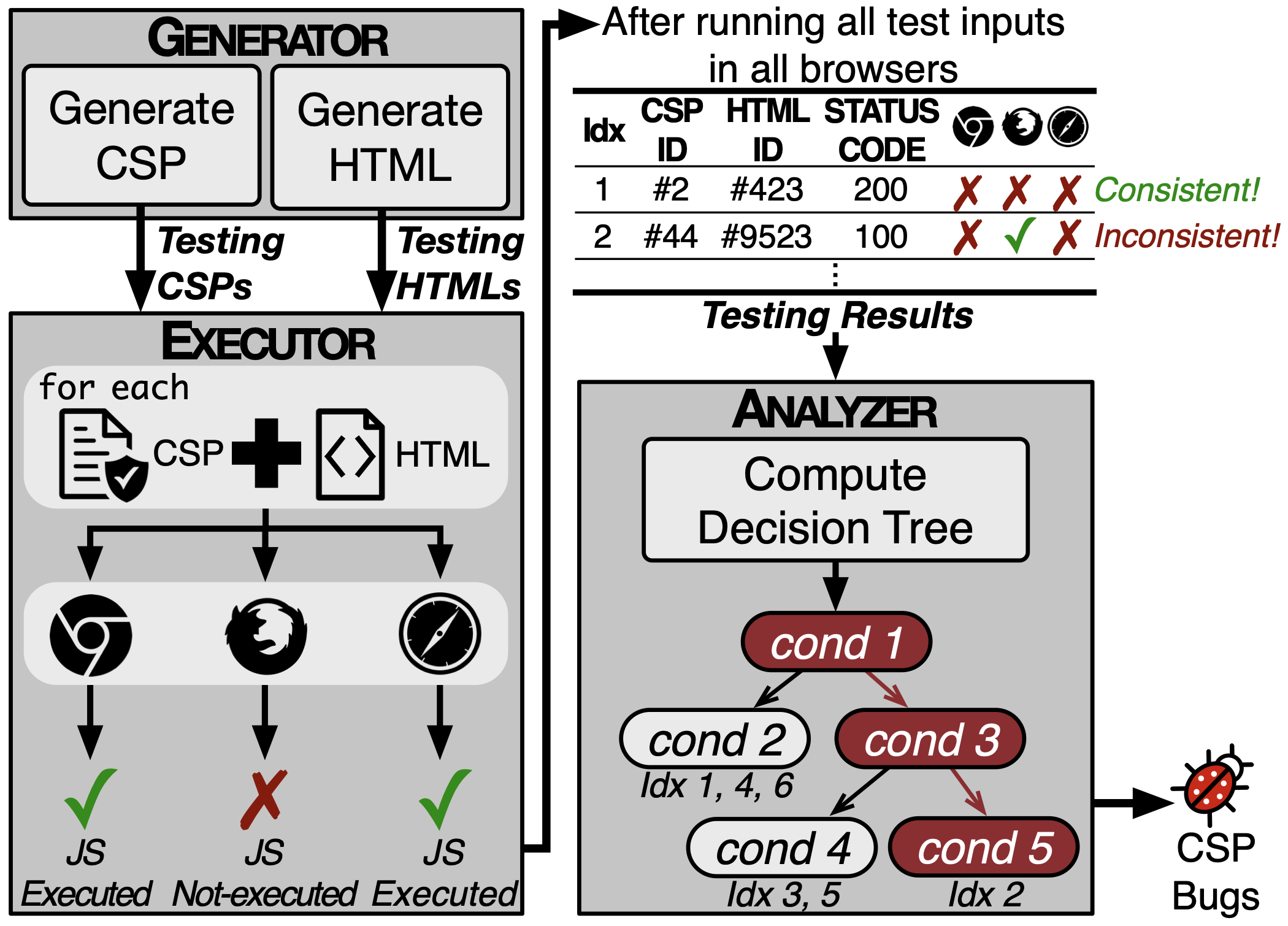
[NDSS'23] DiffCSP: Finding Browser Bugs in Content Security Policy Enforcement through Differential Testing
This paper proposes DiffCSP, the first differential testing framework to find Content Security Policy (CSP) enforcement bugs involving JS execution. DiffCSP generates CSPs and a comprehensive set of HTML instances that exhibit all known ways of executing JS snippets. DiffCSP then executes each HTML instance for each generated policy across different browsers, thereby collecting inconsistent execution results. We demonstrate the efficacy of DiffCSP by finding 29 security bugs and eight functional bugs. We further identify the common root causes of CSP enforcement bugs. We confirm the risky trend of client browsers deriving completely different interpretations from the same CSPs, which raises security concerns. Our findings have contributed to patching 12 security bugs in major browsers, including Chrome and Safari.
[paper]
[code]
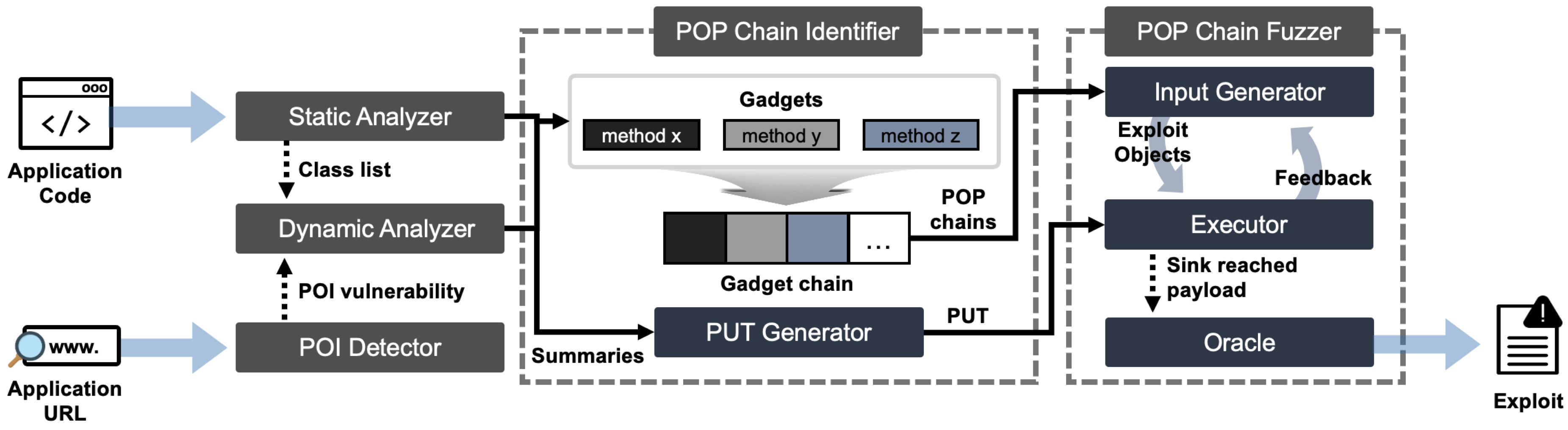
[USENIX Security'22] FUGIO: Automatic Exploit Generation for PHP Object Injection Vulnerabilities
Exploiting a PHP object injection (POI) vulnerability often requires sophisticated property-oriented programming to shape an injection object. Existing off-the-shelf tools focus only on identifying potential POI vulnerabilities without confirming the presence of any exploit objects. To this end, we propose FUGIO, the first automatic exploit generation (AEG) tool for POI vulnerabilities. FUGIO conducts coarse-grained static and dynamic program analyses to generate a list of gadget chains that serve as blueprints for exploit objects. FUGIO then runs fuzzing campaigns using these identified chains and produces exploit objects. FUGIO generated 68 exploit objects from 30 applications containing known POI vulnerabilities with zero false positives. FUGIO also found two previously unreported POI vulnerabilities with five exploits, demonstrating its efficacy in generating functional exploits.
[paper]
[code]
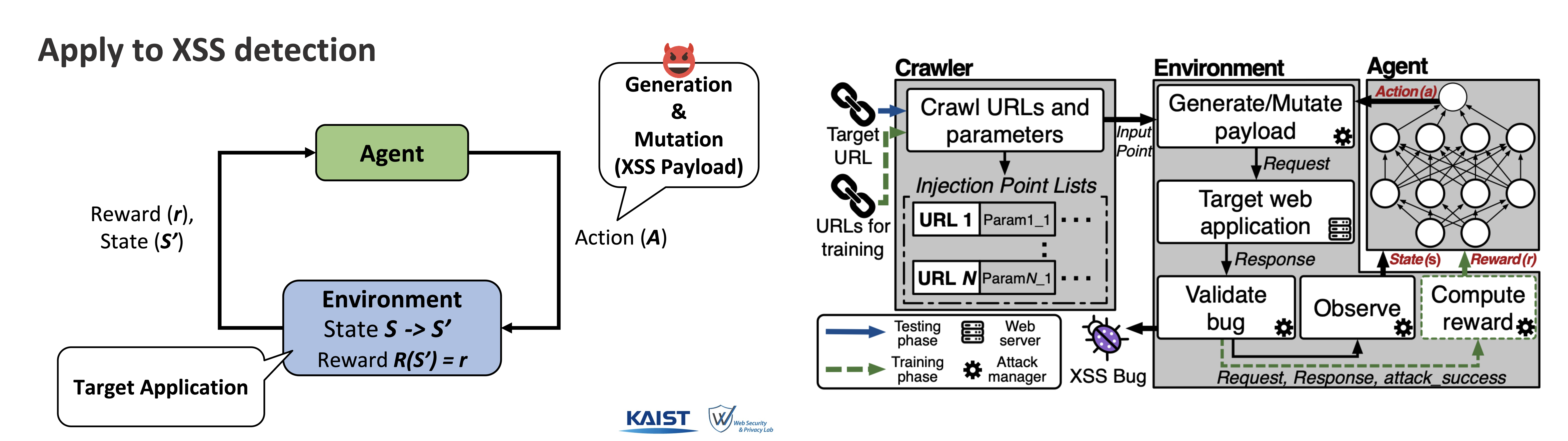
[WWW'22] Link: Black-Box Detection of Cross-Site Scripting Vulnerabilities Using Reinforcement Learning
Off-the-shelf black-box web scanners suffer from unscalable testing as well as false negatives that stem from a testing strategy that employs fixed attack payloads, thus disregarding the exploitation of contexts to trigger vulnerabilities. To this end, we propose a novel method of adapting attack payloads to a target reflected XSS vulnerability using reinforcement learning (RL). We present Link, a general RL framework whose states, actions, and a reward function are designed to find reflected XSS vulnerabilities in a black-box and fully automatic manner. Link finds 45, 213, and 60 vulnerabilities with no false positives in Firing-Range, OWASP, and WAVSEP benchmarks, respectively. Link also finds 43 vulnerabilities in 12 real-world applications, demonstrating the promising efficacy of using RL in finding reflected XSS vulnerabilities.
[paper]
[code]
[WWW'22] HiddenCPG: Large-Scale Vulnerable Clone Detection Using Subgraph Isomorphism of Code Property Graphs
[NDSS'21] The Abuser Inside Apps: Finding the Culprit Committing Mobile Ad Fraud
[USENIX Security'20] Montage: A Neural Network Language Model-Guided JavaScript Engine Fuzzer
[NDSS'20] FUSE: Finding File Upload Bugs via Penetration Testing
R3. Finding security/privacy vulnerabilities in web services
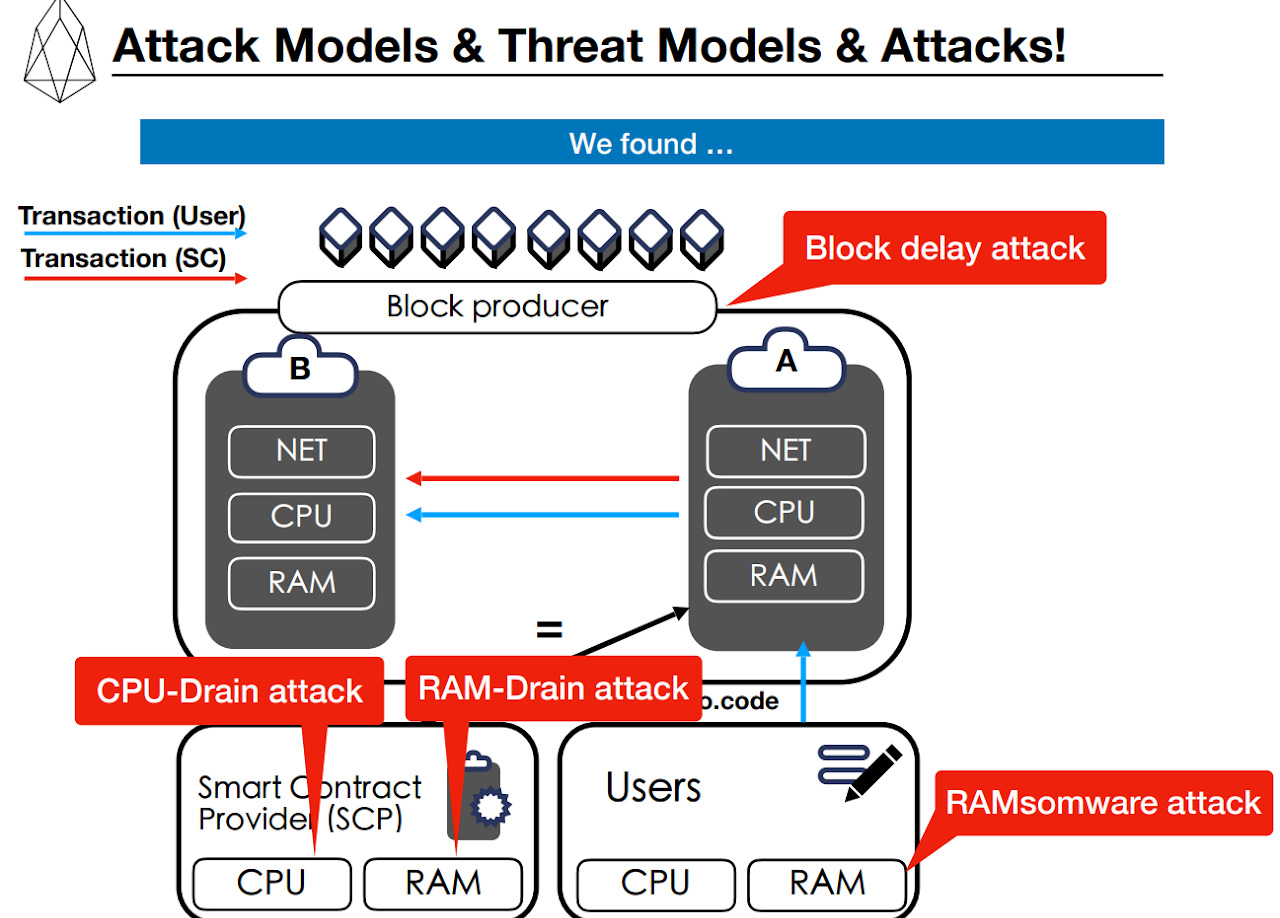
[USENIX WOOT'19] Who Spent My EOS? On the (In)Security of Resource Management of EOS.IO
We investigate the design architecture of EOS.IO. Based on this investigation, we introduce four attacks whose root causes stem from the unique characteristics of EOS.IO, including intentionally slowing down the block creation time—which can disrupt the essential functions of its blockchain and incapacitate the entire EOS.IO system. We also find that an adversary can partially freeze the execution of a target smart contract or maliciously consume all the resources of a target user with crafted requests. We report all the identified threats to the EOS.IO foundation, one of which is confirmed to be fatal. Finally, we discuss possible mitigations against the proposed attacks.
[paper]
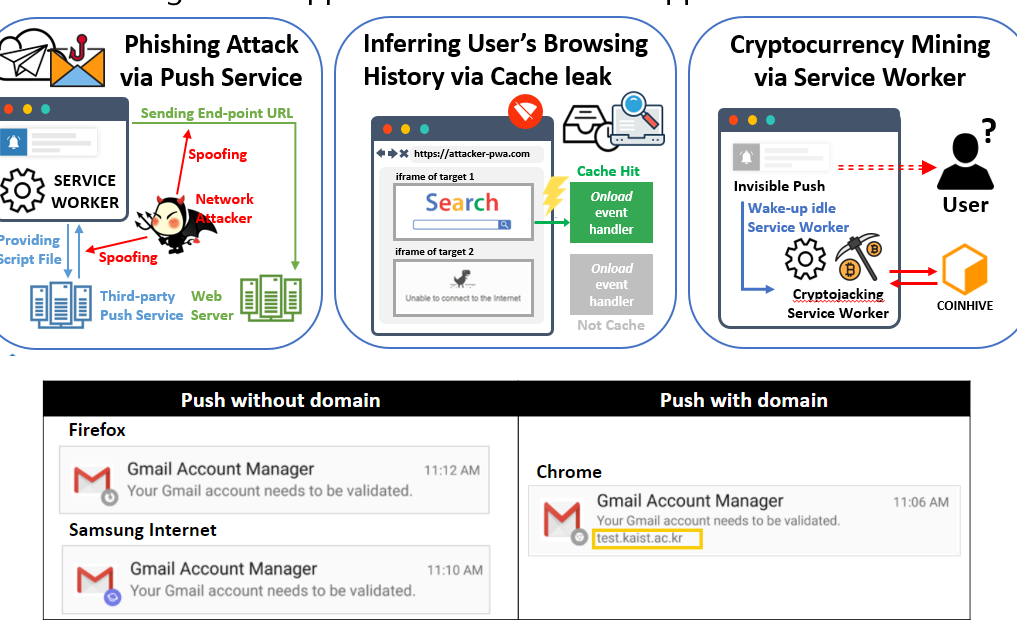
[CCS'18] Pride and Prejudice in Progressive Web Apps: Abusing Native App-like Features in Web Applications
Progressive Web App (PWA) is a new generation of Web application designed to provide native app-like browsing experiences even when a browser is offline. We conduct the first systematic study of the security and privacy aspects unique to PWAs. We identify security flaws in main browsers as well as design flaws in popular third-party push services, that exacerbate the phishing risk. We introduce a new side-channel attack that infers the victim’s history of visited PWAs. The proposed attack exploits the offline browsing feature of PWAs using a cache. We demonstrate a cryptocurrency mining attack which abuses service workers. Defenses and recommendations to mitigate the identified security and privacy risks are suggested with in-depth understanding.
[paper]
[code]
R4. Analyzing online scam/criminal activities occurring on the Internet
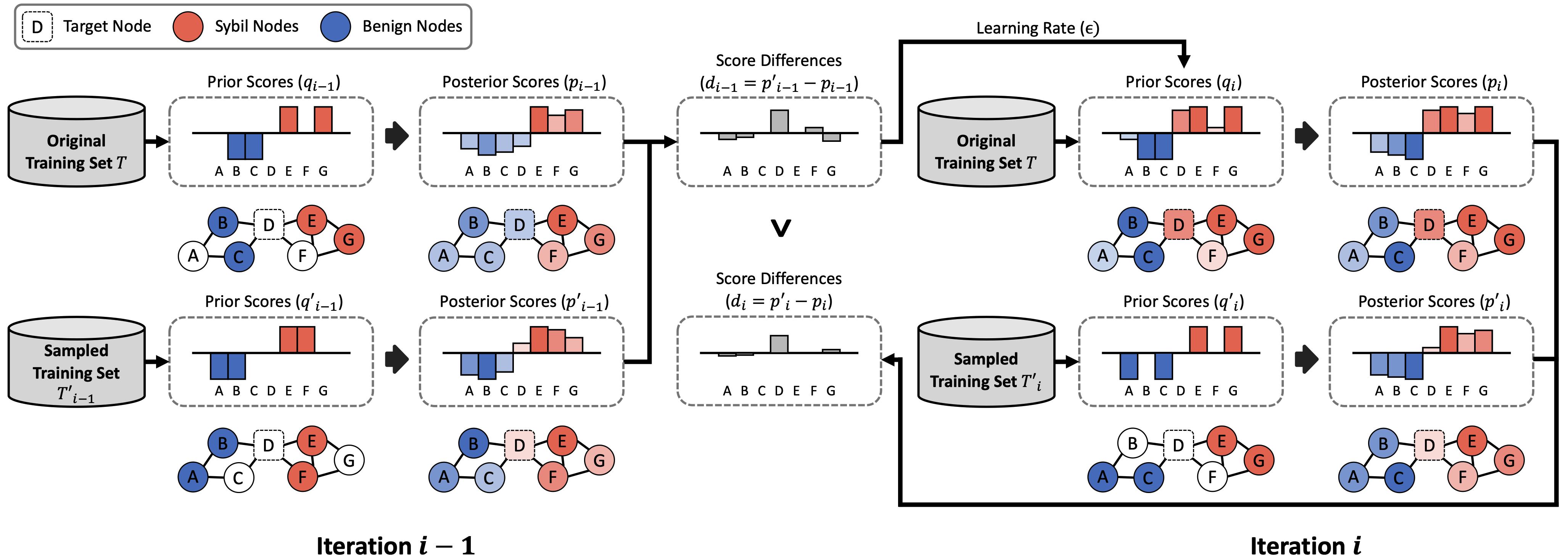
[WWW'23] RICC: Robust Collective Classification of Sybil Accounts
A Sybil attack is a critical threat that undermines the trust and integrity of web services by creating and exploiting a large number of fake (i.e., Sybil) accounts. To mitigate this threat, previous studies have proposed leveraging collective classification to detect Sybil accounts. Recently, researchers have demonstrated that state-of-the-art adversarial attacks are able to bypass existing collective classification methods. To this end, we propose RICC, the first robust collective classification framework, designed to identify adversarial Sybil accounts created by adversarial attacks. RICC significantly outperforms all existing Sybil detection methods, demonstrating superior robustness and efficacy in the collective classification of Sybil accounts.
[paper]
[code]
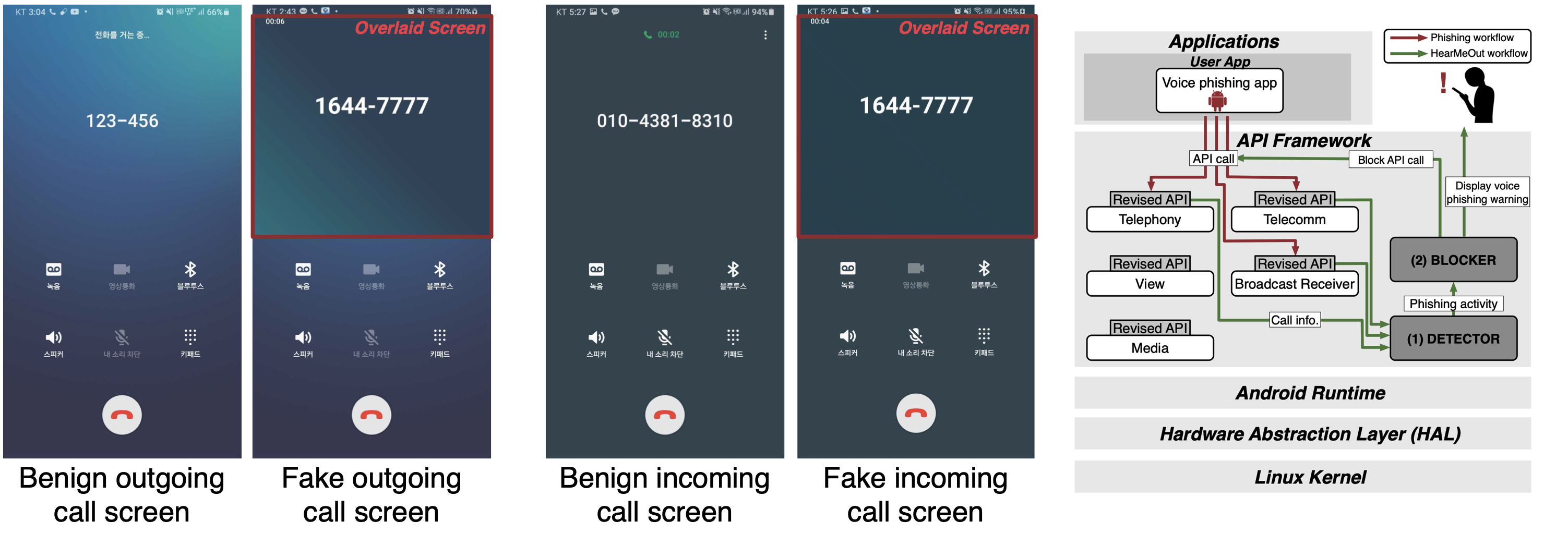
[MobiSys'22] HearMeOut: Detecting Voice Phishing Activities in Android
In South Korea, voice phishing has been proliferating with the advent of voice phishing apps. However, the voice phishing functionalities that these abusive apps implement are largely understudied. To this end, we analyze 1,017 voice phishing apps and reveal new phishing functionalities: outgoing call redirection, call screen overlay, and fake call voice. We further investigate implementations of these fatal functionalities to distinguish their malicious behaviors from their corresponding behaviors in benign apps. We then propose HearMeOut, an Android system-level service that detects phishing behaviors that phishing apps conduct in runtime and blocks the detected behaviors. HearMeOut achieves high accuracy with no false positives or negatives in classifying phishing behaviors while exhibiting an unnoticeable latency of 0.36 ms on average. Our user study demonstrates that HearMeOut is able to prevent 100% of participants from being phished by providing active warnings.
[paper]
[code]
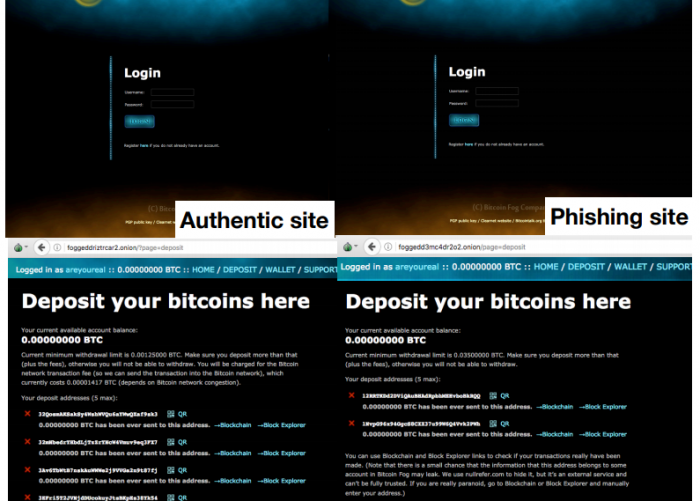
[WWW'19] Doppelgängers on the Dark Web: A Large-scale Assessment on Phishing Hidden Web Services
We conducted an in-depth measurement study to demystify the prevalent phishing websites on the Dark Web. We analyzed the text content of 28,928 HTTP Tor hidden services hosting 21 million dark webpages and confirmed 901 phishing domains. We also discovered a trend on the Dark Web in which service providers perceive dark web domains as their service brands. This trend exacerbates the risk of phishing for their service users who remember only a partial Tor hidden service address. Our work facilitates a better understanding of the phishing risks on the Dark Web and encourages further research on establishing an authentic and reliable service on the Dark Web.
[paper]
[summary]